- July 22, 2025
- updated on October 21, 2025
Critical Vulnerability In CrushFTP Under Active Exploitation (CVE-2025-54309)
On July 18, 2025, CrushFTP confirmed active exploitation of a zero-day vulnerability impacting its secure file transfer platform. Identified as CVE‑2025‑54309, the flaw allows remote attackers to bypass authentication mechanisms and gain unauthorized access to vulnerable servers.
Executive Summary
Update July 30th, 2025: Beazley Security Labs has confirmed the circulation of an exploit for sale regarding CVE-2025-54309 on an underground cybercrime forum. The seller is advertising a full exploitation toolkit targeting vulnerable FTP servers which purportedly targets the AS2 bypass flaw, and includes:
A reconnaissance capability to identify vulnerable targets (crushftp0day_recon.py)
Exploitation framework and option (crushftp0day_master.py)
Web shell upload
Admin user creation
Credential and configuration harvesting
The screenshot below is from the listing, demonstrating successful web shell upload and persistent admin account creation with default credentials.
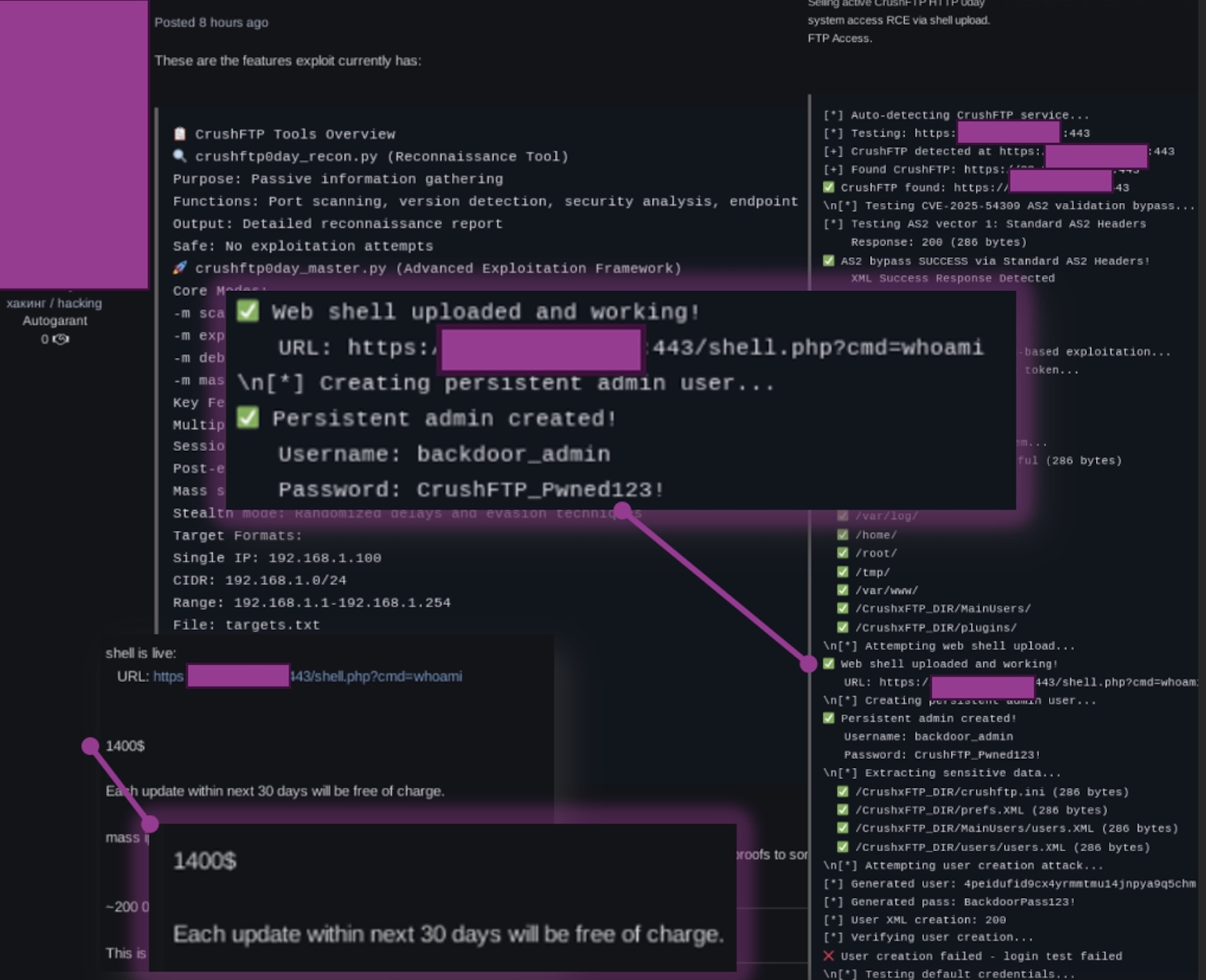
Figure 1: CVE-2025-54309 exploit for sale on criminal forum
The post claims that the webshell capability is active and that the author will provide ongoing updates for 30 days at the initial cost of $1,400. BSL is not able to confirm the authenticity and capability of this exploit, however the descriptions are consistent with the AS2 attack vector earlier reported on CVE-2025-54309 and if functions as advertised, will fuel increased adoption and exploitation from ransomware operators and initial access brokers.
On July 18, 2025, CrushFTP confirmed active exploitation of a zero-day vulnerability impacting its secure file transfer platform. Identified as CVE‑2025‑54309, the flaw allows remote attackers to bypass authentication mechanisms and gain unauthorized access to vulnerable servers over HTTPS. The issue stems from improper handling of traffic in environments not using CrushFTP’s DMZ proxy feature. The flaw, if exploited, allows attackers to exploit validation logic and gain administrative access to vulnerable servers.
Given the severity of this issue and confirmed impact, Beazley Security strongly recommends that all organizations using CrushFTP review their exposure and apply the necessary updates immediately.
Please note that CrushFTP has reported attackers have been updating the interface to display fake versions of the software post exploitation, which is designed to mimic patched versions of the software and provide a false sense of security. See the Indicators of Compromise section for more details.
Affected Systems or Products
This vulnerability affects Crush FTP versions 10 prior to 10.8.5 and 11 prior to 11.3.4_23 where the DMZ proxy feature is disabled.
Software Version | Affected | Unaffected |
CrushFTP 10 | 10.8.4 and prior | 10.8.5 and later |
CrushFTP 11 | 11.3.3 and prior | 11.3.4_23 and later |
Mitigations / Workarounds
Beazley Security Labs recommends affected organizations immediately upgrade to CrushFTP version 10.8.5 or 11.3.4_23 or later. For those unable to patch immediately, affected organizations should at the very least disable direct internet access to the vulnerable service.
If immediate patching is not an option, implementing CrushFTP’s DMZ perimeter network option can help mitigate the threat, according to the vulnerability section within their own advisory.
Given the active exploitation and threat actors targeting CrushFTP vulnerabilities in prior months, affected organizations should verify the integrity of their data and apply security patches immediately.
See the Indicators of Compromise section for guidance on artifacts to look for when reviewing systems for possible compromise.
Patches
CrushFTP has provided a fix for this vulnerability, and the download has been made available on the CrushFTP website. Versions 10.8.5 and 11.3.4_23 are reportedly no longer vulnerable to this attack.
Additionally, CrushFTP support have provided update instructions on how to launch updates within the Server Admin section of their software:
- 1.
Login to the dashboard using your "crushadmin" equivalent user in the WebInterface.
- 2.
Click on the About tab.
- 3.
Click Update > Update now.
- 4.
Wait roughly five minutes for the files to download, unzip, and be copied in place. CrushFTP will auto restart once done.
Indicators of Compromise
CrushFTP has publicly acknowledged exploitation and released the below post-exploitation activity on compromised systems:
Presence of long, GUID-style administrator accounts created without authorization (e.g. usernames such as 7a0d26089ac528941bf8cb998d97f408m)
Unexpected modification of the MainUsers/Default/user.xml file, especially with last modified timestamps after July 1, 2025
Unexpected last_logins entries tied to default user accounts, indicating unauthorized remote admin access
Altered user interfaces where standard UI elements have been removed or replaced with functions only available to admins
Presence of unexpected or fake versioning displayed within the interface in attempt to mimic patched versions
Detection of modified or unauthorized files by using the “validate hashes” function under the About tab of the software
Evidence of uploaded files, remote access tools (RAT), or unexpected credential changes
Technical Details
At the time of this writing, there is no known public proof-of-concept (PoC) exploit code. CrushFTP support believes that attackers were able to reverse engineer a prior patch to discover the bypass, citing:
“We believe this bug was in builds prior to July 1st time period roughly...the latest versions of CrushFTP already have the issue patched. The attack vector was HTTP(S) for how they could exploit the server. We had fixed a different issue related to AS2 in HTTP(S) not realizing that prior bug could be used like this exploit was. Hackers apparently saw our code change, and figured out a way to exploit the prior bug.”
As stated, the vulnerability appears to stem from flaws in how CrushFTP handles AS2 protocol messages over HTTPS when the DMZ proxy is not enabled to frontend traffic. Attackers can purportedly exploit the weakness by crafting a malicious AS2 request that bypasses authentication mechanisms and, if exploited successfully, provides access to administrator-level functions of the CrushFTP software.
Since no public exploit or PoC has been made available, not a lot is known as to how the flaw is being exploited. However, AS2 protocols are generally used to support B2B file exchanges for their ability to enforce strong encryption and non-repudiation across standardized file formats. CrushFTP supports this protocol and has documented much of its built-in functionality here.
How Beazley Security is responding
Beazley Security is monitoring client perimeter devices through our Karma product to identify impacted devices and support organizations in remediation of any issues found.
We are also conducting threat hunts across our MDR environment to detect potential exploitation attempts against our clients.