- June 29, 2024
Critical Vulnerability in FileCatalyst Workflow (CVE-2024-5276)
On June 25th, software company Fortra disclosed a critical severity vulnerability in their managed file transfer software application, FileCatalyst Workflow. The vulnerability is being tracked as CVE-2024-5276 which is an SQL Injection vulnerability that allows an attacker to modify application data.
Executive Summary
On June 25th, software company Fortra disclosed a critical severity vulnerability in their managed file transfer software application, FileCatalyst Workflow. The vulnerability is being tracked as CVE-2024-5276 which is an SQL Injection vulnerability that allows an attacker to modify application data. File transfer applications are typically deployed exposed to the Internet, and a compromise of this system can grant remote attackers a foothold into an organizations internal network.
On May 15, third-party security company Tenable reached out to Fortra regarding a new vulnerability they found in there FileCatalyst Workflow software. FileCatalyst Workflow is a widely used file transfer acceleration solution that offers a web portal to streamline large file exchanges, enhancing business productivity. An attacker can utilize a script to implement the injection and execute an undesired SQL command, including table deletion or creating an admin-level user. The vulnerability can be exploited without authentication if anonymous access is enabled on the Workflow system. Otherwise, an authenticated user is required for exploitation. Additionally, admin-level user has privileges that may affect other FileCatalyst components within your deployment. No threat actors are known to be attacking this vulnerability at the time of writing, however Tenable published proof of concept (PoC) exploit code, and we expect financially motivated threat actors to develop and deploy their own weaponized exploits in the coming days.
Given these factors, Beazley Security believes immediate deployment of Fortra released software patches or mitigation is crucial.
Affected Systems or Products
The vulnerability affects the following Fortra products:
FileCatalyst Workflow up to v5.1.6 build 135
Mitigations / Workarounds
Fortra has provided a mitigation around this vulnerability at the time of disclosure. Users that cannot fully remediate at this time should follow the mitigation steps below to disable the vulnerable servlets for FileCatalyst Workflow.
- 1.
Stop Tomcat Service
- 2.
Navigate to the “web.xml” file located at:
- 1.
<tomcat install dir>/webapps/workflow/WEB-INF/web.xml
- 3.
Backup the web.xml to a safe location before making changes
- 4.
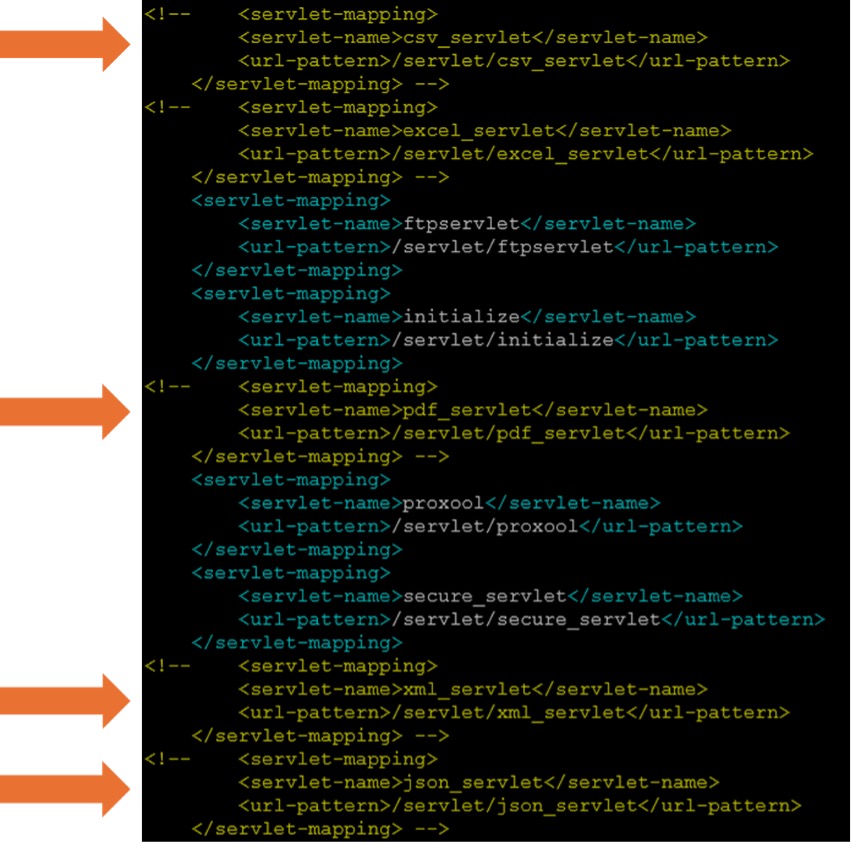
Edit the file and comment out the servlet mapping blocks (as shown in the below screenshot) for:
- 1.
csv_servlet, pdf_servlet, xml_servlet, json_servlet
- 5.
Save the changes and start your Tomcat Service
Patches
Fortra has provided patch instruction in their advisory. To fully remediate the vulnerability, you will need to upgrade FileCatalyst Workflow to version 5.1.6 build 139 or newer. FileCatalyst Workflow downloads are located here.
How Beazley Security is responding
Beazley Security is monitoring client perimeter devices discovered by our Attack Surface Management Solution, Karma, to identify potentially impacted devices and support organizations in remediation of any issues found.